Now - 23:26:19
Network topology: advantages and disadvantages
What are the network topologies? Why are they necessary? Where they are used and for what purpose? What are their types and types exist? Is it possible somehow to neutralize the negative aspects of network topologies and enhance the positive? Here is a short list of questions that will be answered in this article.
General information
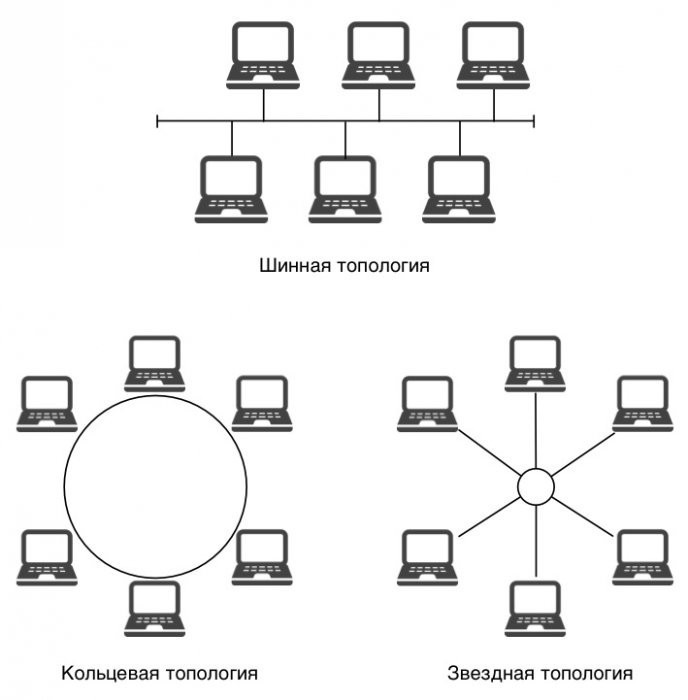 A Lot of people know about the network device. The topology is the same for most – the dark forest. So, let's imagine a small model. We have computers that operate within the same local network. They are connected via communication lines. Depending on the construction of their interaction, the following types of networks:
A Lot of people know about the network device. The topology is the same for most – the dark forest. So, let's imagine a small model. We have computers that operate within the same local network. They are connected via communication lines. Depending on the construction of their interaction, the following types of networks:
- Koltsevoy.
- Zvezdnuyu.
- Sinnou.
- Ierarkhicheskaya.
- Proizvoljno.
All the above relates to the physical topology. But there are also logical. They are independent one from the second. Thus, under the first involves the geometry of building a network. Logical topology deals with the fact that directs the flow of data between different nodes of a network and selects a transfer method of data. Each of the following types of building relationship has its own characteristics, advantages and disadvantages. Now let's consider the basic network topology.
Bus typology
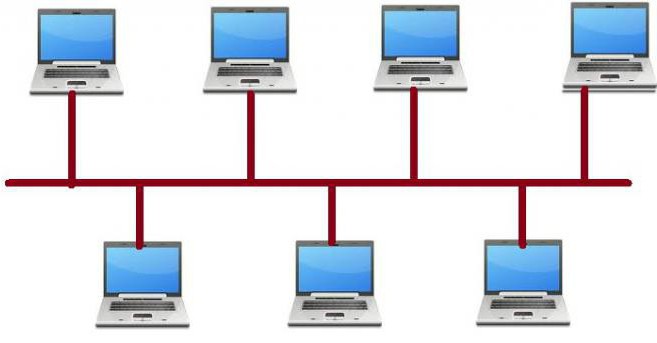 It is used in cases when used for data transmission lineechny a single channel. At its ends set the terminators. Then each computer is connected to the linear broadcast by a T-connector. Data is transferred on both sides and reflect off the EOL terminators. How can we understand the information in this case comes on all the available nodes. But adopted it can only be those for which intended. The medium in this case is used by all personal computers that are connected to the network. And the signal that goes from one PC is distributed on all devices. The popularity of this technology has found when using architecture Ethernet. What are the advantages offered by this equipment (networks)? First we need to mention the ease of setup and network configuration. Also, if fails one node, it will be able to continue its work as a whole. Thanks to this we can say that networks based on the tire type, have considerable resistance to malfunctions. But there are drawbacks. First need to note the restrictions on cable length and number of workstations. Moreover, the gap is linear mono channels adversely affect the performance of the entire network. As a result, it is often difficult to determine the location of the defect, especially if it is covered by insulation.
It is used in cases when used for data transmission lineechny a single channel. At its ends set the terminators. Then each computer is connected to the linear broadcast by a T-connector. Data is transferred on both sides and reflect off the EOL terminators. How can we understand the information in this case comes on all the available nodes. But adopted it can only be those for which intended. The medium in this case is used by all personal computers that are connected to the network. And the signal that goes from one PC is distributed on all devices. The popularity of this technology has found when using architecture Ethernet. What are the advantages offered by this equipment (networks)? First we need to mention the ease of setup and network configuration. Also, if fails one node, it will be able to continue its work as a whole. Thanks to this we can say that networks based on the tire type, have considerable resistance to malfunctions. But there are drawbacks. First need to note the restrictions on cable length and number of workstations. Moreover, the gap is linear mono channels adversely affect the performance of the entire network. As a result, it is often difficult to determine the location of the defect, especially if it is covered by insulation.
Recommended
How to get out of "Skype" on the "Android" and not only
How to get out of "Skype" "Android"? This question bothers many users. The thing is that the messenger is not so difficult. But there are features that are only for mobile versions. To log out of Skype in this case more difficult than it seems. But i...
Kingo ROOT: how to use the program to gain administrative rights on Android
The Gadgets on the platform Android regained the lion's share of the market. Developers are continually perfecting the OS, trying to fit the needs of the users, but from year to year admit palpable mistake: forbid the owner to "stuffing" of his gadge...
How to get from Stormwind to Tanaris: practical tips
World of Warcraft is an iconic MMORPG, uniting millions of players around the world. There are many locations and puzzles, secret trails and larger, but rather dangerous paths. Sooner or later, every player chose the side of the Alliance, we have to ...
Network topology “Star”
 In this case, twisted pair each workstation connected to the hub or hub. Thanks to them provided by the parallel connection of all the personal computer. Through the hub or hub PC and communicate with each other. Sent data arrives at all workstations. But to accept only that for which they were intended. Regarding advantages, it is worth noting that network easy to connect a new personal computer. Also it is resistant to failures of individual nodes and the connection breaks. And complements all this is the possibility of centralized control. However, there are certain disadvantages. So, there is a significant flow of the cable. In addition, the failure of the hub or the hub will affect the entire network.
In this case, twisted pair each workstation connected to the hub or hub. Thanks to them provided by the parallel connection of all the personal computer. Through the hub or hub PC and communicate with each other. Sent data arrives at all workstations. But to accept only that for which they were intended. Regarding advantages, it is worth noting that network easy to connect a new personal computer. Also it is resistant to failures of individual nodes and the connection breaks. And complements all this is the possibility of centralized control. However, there are certain disadvantages. So, there is a significant flow of the cable. In addition, the failure of the hub or the hub will affect the entire network.
Central hub
 This network typology is based on the previous network. The main role in this case played a Central hub. It is an intelligent device that provides the serial connection of the different stations on the principle of “exit”, that is, thanks to him, every computer is connected to two workstations. For stability of there are main and backup ring. This allows you to maintain the health of the network even in the presence of significant damage. Problem point just shut off. For the transmission of data uses a special marker. It contains the address of the sender and receiver of information. It should be noted that, in addition to high reliability, this typology also provides equal access to the network to all workstations. But have to pay for everything. In this case it refers to a large consumption of expensive cable and wiring lines.
This network typology is based on the previous network. The main role in this case played a Central hub. It is an intelligent device that provides the serial connection of the different stations on the principle of “exit”, that is, thanks to him, every computer is connected to two workstations. For stability of there are main and backup ring. This allows you to maintain the health of the network even in the presence of significant damage. Problem point just shut off. For the transmission of data uses a special marker. It contains the address of the sender and receiver of information. It should be noted that, in addition to high reliability, this typology also provides equal access to the network to all workstations. But have to pay for everything. In this case it refers to a large consumption of expensive cable and wiring lines.
The Tree
 , This network typology is considered as a combination of several stars. The tree can be in the following States:
, This network typology is considered as a combination of several stars. The tree can be in the following States:
- Active.
- Passive.
- True.
Dependent state should dedicate staff chooses to use Central computers or hubs (hubs). Each choice has its advantages and disadvantages. In the first case we can talk about building a more centralized system with the best handling and the like. But the use of hubs, or hubs, tend to be considerably more beneficial from a resource and financial plan.
Ring topology
 In this case, provides for the connection of communication channels in one indissoluble chain. However, she does not have to resemble a circle. This implies that for data transfer you will use the output of one personal computer that is connected to the input of another computer. Therefore, when information is to start moving in any one particular point, in the end it will be the same after one round. The data in these rings always move in the same direction. To recognize and process a received message can only be the working of the station to which it was addressed. The topology used marker access. It provides for granting the right to use the rings in the prescribed manner. During data transfer use the logical ring. To create and configure this network very easily. But due to the fact that damage in one place can bring it down, in its pure form it is almost not used due to their unreliability. To work in practice can be used various modifications of this typology.
In this case, provides for the connection of communication channels in one indissoluble chain. However, she does not have to resemble a circle. This implies that for data transfer you will use the output of one personal computer that is connected to the input of another computer. Therefore, when information is to start moving in any one particular point, in the end it will be the same after one round. The data in these rings always move in the same direction. To recognize and process a received message can only be the working of the station to which it was addressed. The topology used marker access. It provides for granting the right to use the rings in the prescribed manner. During data transfer use the logical ring. To create and configure this network very easily. But due to the fact that damage in one place can bring it down, in its pure form it is almost not used due to their unreliability. To work in practice can be used various modifications of this typology.
Combinations
They are used in order to reduce or eliminate the negative side when you create a relation between different computers. The most common combined types of network topology are based on star, bus and ring technologies. To understand the situation, you can give some examples. Take for the first star-bus topology. It is the hub. But it can connect not only individual computers but entire bus network segments. Of course, can be used not one hub, but many. Can also be used in architecture building reference (main) bus. The advantage of this combination is that the system administrator can obtain the advantages of both the typologies and easily affect the amount of computers that are connected to the network. Let's look at another example. Considered to be the star-ring topology. It share not computers, and hubs, which are directly connected a computer. Thus, a closed circuit, which combined the advantages of both topologies, and also appears a number of amenities. As an example such, you can give that all hubs can be assembled in one place. This means that the connection point of the cables will be together, and work with them will be greatly simplified.
Conclusion
 Here we have discussed the main types of network topology. Presented in the article the possibility of building a relationship between the different computers are the most popular due to its practicality. But in some cases, you may need more specialized network topology. Development or use of already existing technologies is carried out with all the necessary for correct operation of the characteristics, nuances and aspects. Usually something like that used only for scientific and military installations, while the civil life is more than enough and the most common approaches. After all, the considered network topology is all based on the decades!
Here we have discussed the main types of network topology. Presented in the article the possibility of building a relationship between the different computers are the most popular due to its practicality. But in some cases, you may need more specialized network topology. Development or use of already existing technologies is carried out with all the necessary for correct operation of the characteristics, nuances and aspects. Usually something like that used only for scientific and military installations, while the civil life is more than enough and the most common approaches. After all, the considered network topology is all based on the decades!
Article in other languages:
AR: https://tostpost.com/ar/computers/3730-network-topology-advantages-and-disadvantages.html
BE: https://tostpost.com/be/kamputary/6581-setkavyya-tapalog-peravag-nedahopy.html
DE: https://tostpost.com/de/computer/6580-netzwerk-topologie-vorteile-und-nachteile.html
ES: https://tostpost.com/es/los-ordenadores/6586-topolog-as-de-red-ventajas-y-desventajas.html
HI: https://tostpost.com/hi/computers/3732-network-topology-advantages-and-disadvantages.html
JA: https://tostpost.com/ja/computers/3731-network-topology-advantages-and-disadvantages.html
PL: https://tostpost.com/pl/komputery/6586-topologiach-sieciowych-zalety-i-wady.html
PT: https://tostpost.com/pt/computadores/6582-a-topologia-da-rede-vantagens-e-desvantagens.html
TR: https://tostpost.com/tr/bilgisayarlar/6587-a-topolojisi-avantajlar-ve-dezavantajlar.html
UK: https://tostpost.com/uk/komp-yuteri/6585-merezhev-topolog-perevagi-ta-nedol-ki.html
ZH: https://tostpost.com/zh/computers/4002-network-topology-advantages-and-disadvantages.html

Alin Trodden - author of the article, editor
"Hi, I'm Alin Trodden. I write texts, read books, and look for impressions. And I'm not bad at telling you about it. I am always happy to participate in interesting projects."
Related News
The most common in practice are which database?
Working with the database accompanies any more or less complex project. The database acts as a repository of information containing everything necessary for the correct working of the system parameters. And what practices most com...
Skyrim: how to become a vampire?
there are Few people who do not recognize that to play Skyrim - a pleasure! Huge world, awesome texture, endless quests, beautiful battles and incredible opportunities - all this attracts players to such an extent that they someti...
How to find whose IP address in "Contact"? Secrets revelations over IP
Today we will try to figure out how to find whose IP address you have in "Vkontakte" appeared after the test sessions. Sometimes this basis it is possible to calculate the attacker page. Search people by IP address is very popular...
Object 140: guide and review. Object 140 World of Tanks: specifications
In the game WoT a lot depends on how properly you choose the tank and as well develop a strategy around it. The fact that this game has no pulse, that is, machines which in any case are better than the rest - each has its pros and...
The System process (NT Kernel System) bad: what to do? Some practical recommendations
it so Happens that the user in the system like any resource-intensive programs are not running anything lately, not installed, and the load on the CPU and RAM suddenly increases enormously (albeit briefly). The culprit, if you loo...
Nvidia Geforce 210: a review of the graphics card
the competition on the market of discrete graphics cards does not stop for a minute. Recently the clear leader was Nvidia, which could provide a model for any need. Eventually joined the race and AMD, which, I must say, it came ou...



















Comments (0)
This article has no comment, be the first!