Now - 21:01:42
Cryptographer paycrypt@gmail.com: how to decipher
As you know, viruses and malwares on the world wide web every day appears more and more. But today the consequences of their impacts go far beyond the violation of the system. More and more attackers start to extort money. Such threats include virus paycrypt@gmail_com, who is a cryptographer. He appeared relatively recently, so the fight against it-it quite time consuming.
What is a virus paycrypt@gmail_com?
In principle, she “infection” working on the thumb of the algorithm applied in the most famous viruses like CBF, XTBL and I Love You.

Without going into the pattern of his work, we can say only one thing: the consequences of its impact lies in the fact that all of your files and documents are encrypted with a special algorithm, which the hackers themselves referred to as RSA-1024. Ultimately, after encrypting any document or user file without a special key can open.
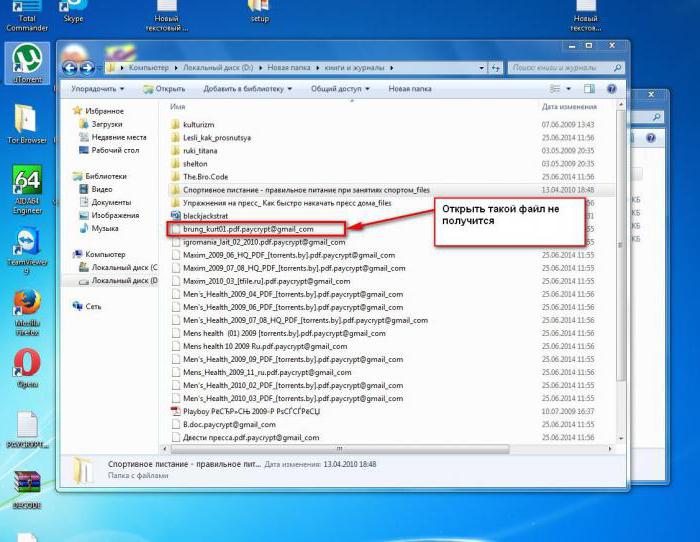
File names in addition to the existing extension prescribed paycrypt@gmail_com. How to decrypt such files (and if it's even possible), we will now see.
How a virus penetrates into the system?
The Penetration of threats on a separate terminal or even in a local network can be accomplished in several ways. The most common are e-mail attachments that contain programs-loaders that could catch the virus directly on the infected website, or hidden objects that are activated when you copy information from removable media. Sometimes it can be “catch” even just clicking on the advertising banner.
Recommended
How to get out of "Skype" on the "Android" and not only
How to get out of "Skype" "Android"? This question bothers many users. The thing is that the messenger is not so difficult. But there are features that are only for mobile versions. To log out of Skype in this case more difficult than it seems. But i...
Kingo ROOT: how to use the program to gain administrative rights on Android
The Gadgets on the platform Android regained the lion's share of the market. Developers are continually perfecting the OS, trying to fit the needs of the users, but from year to year admit palpable mistake: forbid the owner to "stuffing" of his gadge...
How to get from Stormwind to Tanaris: practical tips
World of Warcraft is an iconic MMORPG, uniting millions of players around the world. There are many locations and puzzles, secret trails and larger, but rather dangerous paths. Sooner or later, every player chose the side of the Alliance, we have to ...
As is, e-mail – the main tunnel. This does not apply to mail servers, but only the accounts that are used in stationary programs like Outlook or third-party applications installed on computer terminals.
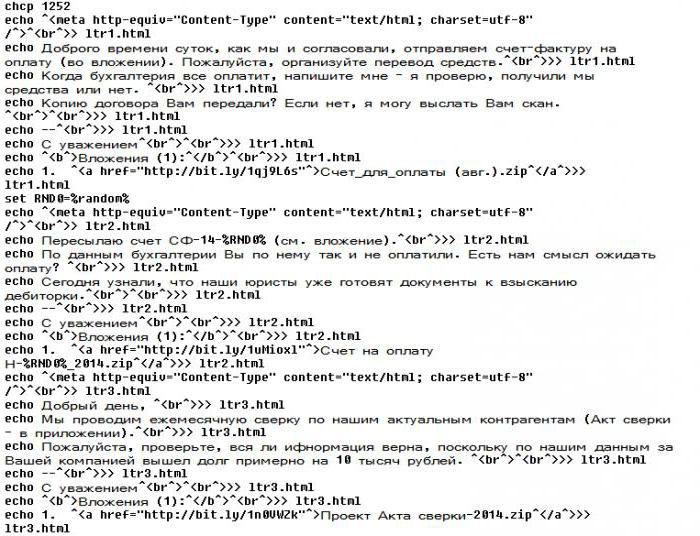
User opens, for example, the message about the change in the contract of supply of products and looks attachment. It has a file. If you see that the extension is unknown, it is better not to open at all. But the PostScript, say, in the attachment contains a scanned copy of the new version of the agreement, all confusing, and the user opens the file, just not even thinking.
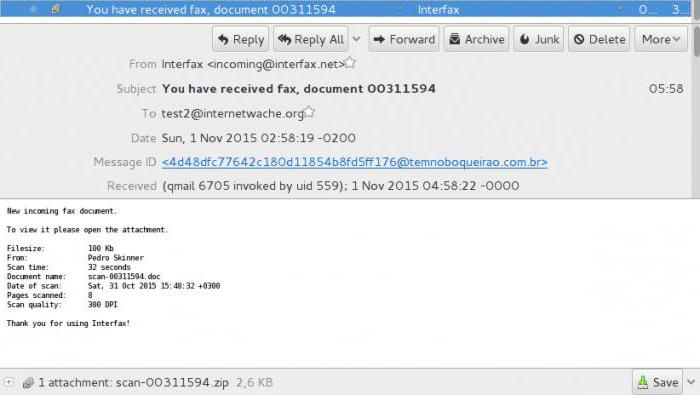
But very often you can find an attachment in a plain text file or Word document. The user clicks on it, and… off we go (note to rename any file, giving it the extension .txt, .extension doc or graphic .jpg you can, as they say, quite elementary. And the system sees a registered file type and then trying to open it).
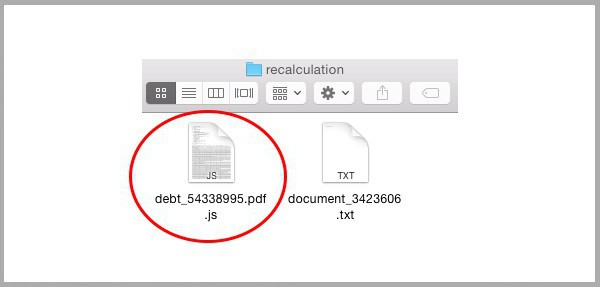
Sometimes in the attachment found in an executable. JS file (Java Script), to open not at all!
The First sign of the impact is instant “inhibition” of a computer. This indicates excessive load on system resources due to the fact that embedded in the file paycrypt@gmail_com malicious code began the encryption process. Incidentally, he can take quite a long time, and no rebooting will not help. If you restart the system, the virus will again begin its dirty work. At the end of the process of getting a fully encrypted files paycrypt@gmail_com. How to decipher them, we naturally do not understand. Manual anticipated actions later proposed by the attackers.
The algorithm for the demands of hackers
The Ordinary users of “catch” the virus, in General, infrequently. Rather, it is focused on businesses and organizations. In this case, if the enterprise has quite an extensive local network, encryption can relate to all terminals connected to the network.
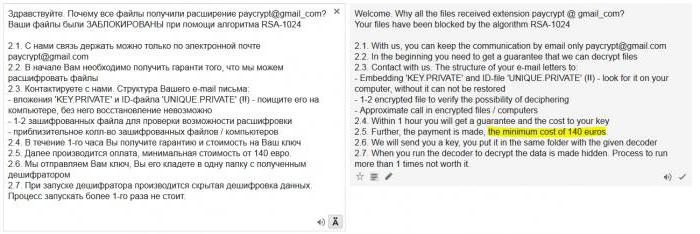
As the instructions that came with the virus paycrypt@gmail_com (how to decrypt the data - it describes), appears an email that says that the files are encrypted with RSA-1024. Next, seemingly with good intentions, the assertion that to decrypt the data can only group who sent the message. But such a service costs about from 100 to 500 euros.
To get paycrypt@gmail_com-interpreter, to the mail address you want to send the KEY file.PRIVATE, and a few infected files. After that it is assumed that the user will have its own unique key. Frankly, believe in it with difficulty.
It is reported that to decrypt the files paycrypt@gmail_com yourself can not even try, because the only solution is a full format of drive or partition. There should be a hint that user data is very important to him, so that the formatting is inappropriate.
Is it Worth to contact the attackers?
Unfortunately, unsuspecting users or owners of the very important information immediately run to pay for the services, but in return get nothing. If at the beginning of the emergence of this threat someone, maybe even received the key, today it is possible even not to dream – normal extorting money.
Some all the same trying to use the anti-virus scanners, but here's the problem-the virus-it really varies, even seems to be treated and removed, but the information remains encrypted.
Are There for the virus paycrypt@gmail_com interpreter?
As for decrypting the data, virtually none of the well-known anti-virus software developed by a particular and a universal solution can not imagine.
You Can search through the entire Internet in search of the key. But nothing good will come of it. The only thing you can try to look for already known keys like unblck@gmail.com, uncrpt@gmail.com, unstyx@gmail.com etc. Perhaps some combination will help, but we should not deceive ourselves.
How to get a utility to decrypt on the official website of the developer of anti-virus?
But let's see what we can do if we caught a virus paycrypt@gmail_com. How to decode it, for example, the user does not know. In such a situation, provided that the computer terminal installed the official (licensed) version of antivirus software, it is better to directly contact the support center developer.
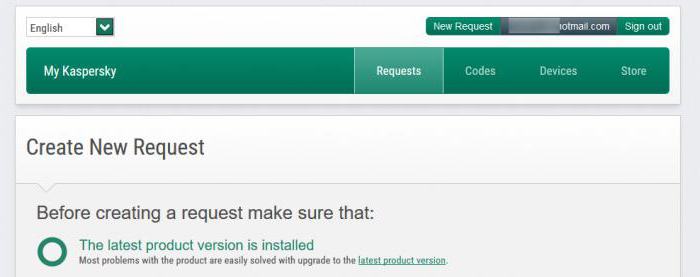
At the same time on the official website should use the section of the request for treatment, and then send a few infected files. If you have an uninfected copy of the original object, even better. In such a situation, the likelihood that the data will be decrypted, is increased many times, as, for example, the virus itself paycrypt@gmail_com “virus” (standard scanner) to cure simply can not.
If all else fails…
If the answer is for any reason not obtained, and to the attackers to turn intentions no, there's nothing you can do about it. The only solution will only format the hard disk. Thus it is necessary to perform a full format, not clearing the table of contents.
We should say that the virus penetrate to the hard drive or logical partition it could create its own copy, so formatting will have absolutely everything that is, and install the system again. There is no other way.
By the Way, and utilities that are loaded before the start of the system (like Kaspersky Rescue Disc) will not help either. As mentioned above, the virus they find, even deletes, but allow the source data in readable condition will not. This is understandable, because originally, even such powerful utility is, in General, and is not intended.
Finally Some tips
That's considered a virus paycrypt@gmail_com. How to decode it? To this question, as is clear, the answer is no. It is better in advance to protect themselves from the penetration of threats to the system.

You should only Open email attachments received from trusted sources should not be in vain to click on the advertising on the Internet. Especially pay attention to the letters in the name of the attached file is gibberish (a set of unreadable characters), but changing the encoding does not help to see the name in the normal view. In General, beware!
Well, needless to say, it makes no sense to pay money to the extortionists, and in return not receive the necessary key. However, it proved quite easy in the case of other known viruses and malicious codes that has ever been recorded in world practice.
...Article in other languages:
AR: https://tostpost.com/ar/computers/10204-paycrypt-gmail-com.html
DE: https://tostpost.com/de/computer/18333-schl-ler-paycrypt-gmail-com-wie-entschl-sseln.html
ES: https://tostpost.com/es/los-ordenadores/18347-el-cifrador-paycrypt-gmail-com-como-descifrar.html
HI: https://tostpost.com/hi/computers/10213-cryptographer-paycrypt-gmail-com.html
JA: https://tostpost.com/ja/computers/10213-cryptographer-paycrypt-gmail-com.html
PL: https://tostpost.com/pl/komputery/18295-shifroval-schik-paycrypt-gmail-com-jak-rozszyfrowa.html
PT: https://tostpost.com/pt/computadores/18297-shifroval-schik-paycrypt-gmail-com-como-decifrar.html
TR: https://tostpost.com/tr/bilgisayarlar/18333-kriptoloji-paycrypt-gmail-com-de-ifre.html
ZH: https://tostpost.com/zh/computers/11063-paycrypt-gmail-com.html

Alin Trodden - author of the article, editor
"Hi, I'm Alin Trodden. I write texts, read books, and look for impressions. And I'm not bad at telling you about it. I am always happy to participate in interesting projects."
Related News
Power Rangers (Dota 2): the composition and history of the team
Power Rangers (Dota 2) - Belarusian eSports team that was founded in 2012. Despite short period of existence, the team has seen a lot. Was and impressive performances in major tournaments (but the money it came rare), and a disast...
Inaccessible Boot Device during Windows 10: how to fix? Recommendations
If you are an experienced computer user, then definitely you have heard about the phenomenon of “blue screen of death”. The so-called error that is associated with the Windows system. The first such problem occurred in...
How to make a potion of instant damage 2 level in Minecraft: manual
in the study of the world of "Minecraft," you not once, not twice useful various potions. Of course, if you play in survival mode without entering commands from the console, then to create a potion you get at the end, when no enem...
Description how to create a server in Minecraft
Now there is hardly a person who has not played or at least heard about a game like "Minecraft". This project was created without expectation of something incredible, but in the end, everything turned out exactly. This game is a "...
Synchronization - what is it and why is it necessary?
Many of us in daily life are confronted with a term such as “sync”. What is this, and why do I need it now and will be considered. Looking ahead, it can be noted that almost all the people know about this term is that ...
How to choose the best anonymizer?
Probably the person who once created the first anonymizer, not even dreamed of how huge the benefits will be to bring his brainchild. Anonymizers, also called “proxy”, there is an equally long time as the global networ...



















Comments (0)
This article has no comment, be the first!