Now - 08:45:14
SIP Protocol: description
The Session Initiation Protocol (SIP) is a Protocol for signaling and control of multimedia communication sessions. The most common applications in Internet telephony-voice and video calls and instant messaging over IP networks (Internet Protocol).
It defines the messages that are sent between endpoints and regulate the establishment, termination and other essential elements of the call. The SIP Protocol, the description of which is presented above, can be used for creating, modifying and terminating sessions consisting of one or more streams of multimedia data. It is a application level Protocol. Designed to be independent of core transport layer. In other words, this Protocol is text-based, incorporating many elements of HTTP (Hypertext Transfer) and Simple Mail Transfer Protocol (SMTP).
SIP Protocol – what is it?
The SIP works in conjunction with several other application-layer protocols that identificeret and transmit a multimedia session. Identification and coordination of media data is achieved in conjunction with the Session Description Protocol (SDP). For transmission of multimedia streams-voice, video, – he usually uses a transport Protocol real-time (RTP) or Secure mode (SRTP). For secure transmission of SIP messages can be encrypted using Transport Layer Security (TLS).
Development History
The SIP Protocol was originally developed by a group of experts in 1996. It was standardized in RFC 2543 in 1999 (SIP 1.0). In November 2000, he was accepted as a signal of the 3 GPP Protocol and permanent element of the IP Multimedia Subsystem architecture (IMS) for multimedia streaming services in IP-based cellular systems. The latest version (SIP 2.0) in RFC 3261 was released in June 2002. With certain extensions and refinements it is used in our time.
Recommended
How to get out of "Skype" on the "Android" and not only
How to get out of "Skype" "Android"? This question bothers many users. The thing is that the messenger is not so difficult. But there are features that are only for mobile versions. To log out of Skype in this case more difficult than it seems. But i...
Kingo ROOT: how to use the program to gain administrative rights on Android
The Gadgets on the platform Android regained the lion's share of the market. Developers are continually perfecting the OS, trying to fit the needs of the users, but from year to year admit palpable mistake: forbid the owner to "stuffing" of his gadge...
How to get from Stormwind to Tanaris: practical tips
World of Warcraft is an iconic MMORPG, uniting millions of players around the world. There are many locations and puzzles, secret trails and larger, but rather dangerous paths. Sooner or later, every player chose the side of the Alliance, we have to ...
Despite the fact that the original SIP Protocol was designed based on voice services. Today it supports a wide range of applications, including videoconferencing, streaming media, instant messaging, file transfer and Fax over IP and online games.
SIP Protocol – description and operation
Session Initiation Protocol depends on the underlying transport Protocol. It runs on Transmission Control Protocol (TCP), user Datagram Protocol (UDP) or transmission control Protocol flow (SCTP). It can be used for data transmission between two parties (unicast) and multicast session.
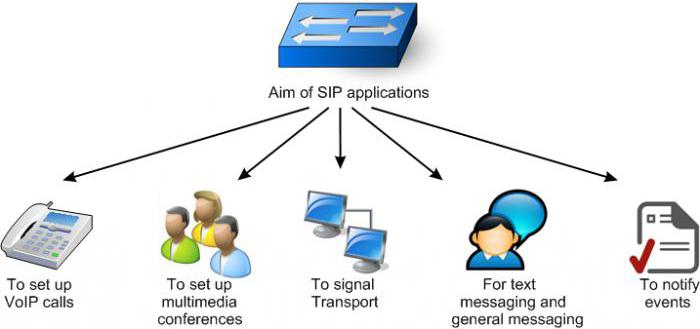
It has design elements similar to the query model of an HTTP transaction. Each such operation consists of a client request that invokes a particular method or function on the server, and at least one answer. The SIP Protocol reuses most of the header fields, encoding rules and status codes of HTTP, providing a readable text format.
Each resource of the network Session Initiation Protocol-user agent or a Voicemail box – recognized by using distribution ID resource identifier (URI), based on the General standard syntax also used in web services and e-mail. The URI scheme used for SIP is a logical chain of: user name: password @ host: port.
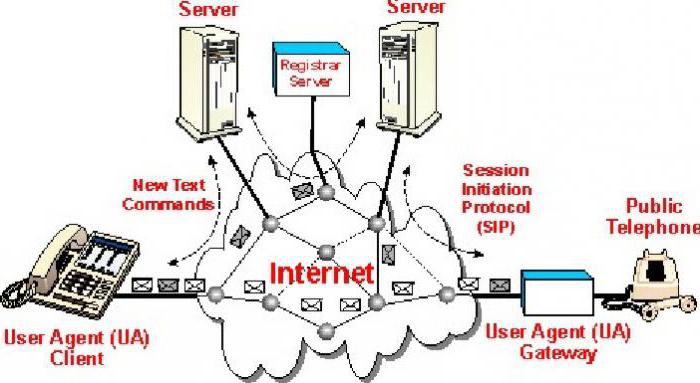
Security Policy
If you need a secure data transmission scheme prescribes that each of the network elements on which the request is redirected to the target domain must be secured with Transport Layer Security (TLS). The last step of the proxy server to the target domain and the obligation to operate in accordance with the local settings for security. TLS protects against attackers who try to capture data in the moment of their submission. But it does not provide real security and can prevent tracking and information theft. How the SIP Protocol, the ports which must be securely coupled, works with other network services?
It works in concert with several other protocols and is only involved in the signaling portion of the communication session. SIP clients typically use TCP or UDP with port numbers 5060 or 5061 to connect to SIP servers and other SIP endpoints. Port 5060 is commonly used for unencrypted signaling traffic whereas port 5061 is closely “friends” with Transport Layer Security (TLS).
What is?
To most accurately answer the question “SIP Protocol – what is it?”, you should understand why it is used. It is typically used to configure and transfer voice or video calls. It allows you to modify existing calls. The modification can involve changing addresses or ports, inviting into the conversation more participants, adding or removing streams of multimedia data. SIP has also found applications in messaging applications and services event subscription and notification.
A Set of SIP rules associated with the Internet Engineering Task Force (IETF) specifies the user manual for such applications. Videophotography voice and message applications are migrated to a different Protocolthe application program in real-time Transport Protocol (RTP). Settings-port numbers, protocols, codecs – for these media streams are defined and agreed upon using the description Protocol session (SDP), which can be moved to the body of a batch Session Initiation Protocol (e.g., SIP-T).
The Main prospect of the development of the Protocol is that it needs in the future to ensure the installation of the alarm system and call for IP communications on the fundamentals that will support supersaber of call handling functions and options present in the public switched telephone network (PSTN). It itself does not define them. Rather, it regulates only call setup and signaling. All actions aimed at the implementation of such telephone operations (i.e., dialing, return ringback tones or a busy signal), are performed by proxy servers and user agents. Implementation and terminology are different in different countries, but they operate on the same principle.
Value telephone
The Telephone network using the SIP Protocol can also implement many of the more advanced call handling functions present in Signaling System 7 (SS7). Although both of these protocols are quite different. SS7 is a centralized Protocol. It is characterized by a complex Central network architecture and “stupid” endpoints (traditional telephones). SIP is the Protocol type "client-server”. However, most devices that support Session Initiation Protocol can perform both the role of client and server. In General, the initiator of the session acts as a client, and the recipient of the call does the server function. Thus, SIP functions are implemented in the communicating endpoints, contrary to traditional SS7 features, which are implemented in the network.

SIP is fundamentally different because the technology develops in the field of IT, not in the telecommunications industry. The SIP Protocol is standardized and is determined mainly by the IETF, while others (e.g., H. 323) traditionally associated with the International telecommunication Union (ITU).
Network elements
SIP defines user agents, as well as several types of network elements of the server. Two SIP endpoints can communicate without any intervening infrastructure. However, this approach is often impractical for the state, which needs directory services to search for available nodes in the network. The SIP Protocol register can not provide such functionality.
User Agent
A user Agent (SIP UA) is a logical network end points. They are used to create or receive messages and thereby manage a SIP session. A SIP UA can perform the role of client user agent (UAC), which sends SIP requests, and a server (UAS) that receives requests and returns a SIP response. So UAC and UAS is only possible within a SIP transaction.
Telephony
SIP phones, in fact, is IP telephony, which implements both client and server function SIP user agent. In addition, it provides the traditional options of telephone call-dial, answer, reject, hold/removing and call forwarding.
SIP phones may be implemented as a hardware device or as a Softphone. As manufacturers increasingly use this Protocol as a standard telephony platforms (in recent years – through 4G), the distinction between hardware and software the basics of SIP phones remain unclear. In addition, elements of Session Initiation Protocol today are implemented in the basic functions of the embedded software of many IP-capable devices. Examples include many devices from Nokia and BlackBerry, and the SIP Protocol on Android is currently the irreplaceable service.

In SIP, as in HTTP, the user agent may identify itself using a message header field User-Agent, containing a textual description of the software/hardware/products. Field user-agent is passed in the request messages. This means that the receiving SIP server can see this information. Network elements Session Initiation Protocol can sometimes store this information. And it can be useful for diagnosing compatibility issues.
Article in other languages:
AR: https://tostpost.com/ar/computers/5069-sip.html
BE: https://tostpost.com/be/kamputary/9025-sip-pratakol-ap-sanne.html
DE: https://tostpost.com/de/computer/9025-sip-protokoll-beschreibung.html
ES: https://tostpost.com/es/los-ordenadores/9031-sip-protocolo-descripci-n.html
HI: https://tostpost.com/hi/computers/5072-sip-protocol-description.html
JA: https://tostpost.com/ja/computers/5069-sip.html
KK: https://tostpost.com/kk/komp-yuterler/9029-sip-hattamasy-sipattamasy.html
PL: https://tostpost.com/pl/komputery/9028-sip-protok-opis.html
PT: https://tostpost.com/pt/computadores/9024-o-protocolo-sip-descri-o.html
TR: https://tostpost.com/tr/bilgisayarlar/9033-sip-protokol-a-klama.html
UK: https://tostpost.com/uk/komp-yuteri/9029-sip-protokol-opis.html

Alin Trodden - author of the article, editor
"Hi, I'm Alin Trodden. I write texts, read books, and look for impressions. And I'm not bad at telling you about it. I am always happy to participate in interesting projects."
Related News
"Boot Manager": what is it in the various OS, how to use it?
the idea is that the so-called Windows boot Manager at the start of the computer is presumed to appear only in the case if on Board there are two or more installed operating systems. However, this is not always the case. For the m...
Flat design or Back to minimalism
the Word "flat" in English means "flat". Since the advent of the so-called Flat design over the last several years continues to hold its position, occupying a leading place in the market. how it all began Web design since its appe...
Call of Duty: all parts in order. Call of Duty series of games
Many computer games are solitary, i.e. they come as a separate product, without background and without potential or actual sequels. There are projects that unite a dilogy or a trilogy. But there's a full series that are published ...
How to make items in Minecraft using workbench?
"Minecraft" is a game in which you will teach, you will not give any settings or tasks, you will not explain what to do and how. You will find yourself in the middle of a huge world full of dangers, without any equipment. Absolute...
Breaking Point: how to install the add-on
Today we decided to talk about the game Breaking Point and tell how to install it. A large number of users face problems that can occur during installation. Not many people know what is Arma 3 Breaking Point how to install the add...
many modern businesses use computer-aided design, or CAD. There are a large number of suppliers of such solutions. The features and capabilities of data design systems, and in particular presented by specialized AT the appropriate...


















Comments (0)
This article has no comment, be the first!