Now - 16:15:27
How to configure and use SSH port? Step by step instructions
Secure Shell or SSH is abbreviated, is one of the most advanced technologies to protect data in transit. The use of such a regime on the same router ensures not only confidentiality of information, but also to accelerate the exchange of packages. However, not everyone knows how to open the SSH port and why do I need it. In this case, you will have to give a constructive explanation.
SSH Port: what is it and why should I?
Since we are talking about security, in this case the SSH port you should understand the selected communication channel in the form of a tunnel that provides data encryption.
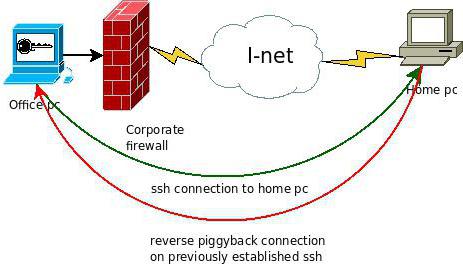
The Most primitive scheme of work of this tunnel is that open SSH port by default is used to encrypt information at the source and decoding at the endpoint. To clarify this: you want this or not transmitted traffic, unlike IPSec, encrypted under compulsion and at the output of the one network terminal, and the receiving party. To decrypt the information transmitted in this channel, the receiving terminal uses special key. In other words, to interfere in the transfer or compromise the integrity of the transmitted data at the moment without the key, nobody can.
Just opening the SSH port on any router or by using appropriate settings of the client that interacts with the SSH server directly, allows you to fully use all the security features of modern networks. It's about how to use the port assigned by default, or custom settings. These parameters in the application may look rather complicated, but without understanding the organization of such a connection is not necessary.
Standard SSH port
If you really start from the settings on any router, the first step is to decide what software will be used to leverage this communication channel. In fact, the SSH port default can have different settings. It all depends on which method is currently applied (direct connection to the server, extra client, port forwarding, etc.).
Recommended
How to get out of "Skype" on the "Android" and not only
How to get out of "Skype" "Android"? This question bothers many users. The thing is that the messenger is not so difficult. But there are features that are only for mobile versions. To log out of Skype in this case more difficult than it seems. But i...
Kingo ROOT: how to use the program to gain administrative rights on Android
The Gadgets on the platform Android regained the lion's share of the market. Developers are continually perfecting the OS, trying to fit the needs of the users, but from year to year admit palpable mistake: forbid the owner to "stuffing" of his gadge...
How to get from Stormwind to Tanaris: practical tips
World of Warcraft is an iconic MMORPG, uniting millions of players around the world. There are many locations and puzzles, secret trails and larger, but rather dangerous paths. Sooner or later, every player chose the side of the Alliance, we have to ...
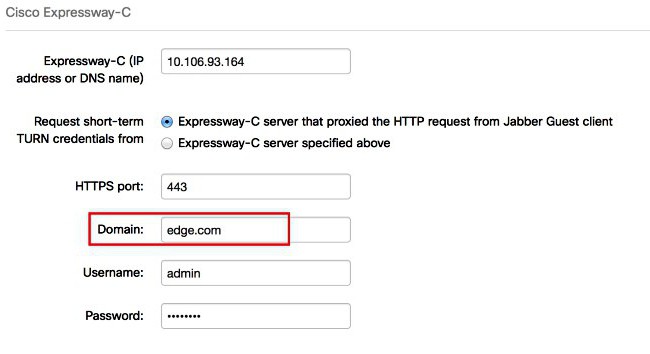
For example, if the Jabber client is used, correct connection, encryption and transfer of data must use port 443, while the standard option is set to port 22.
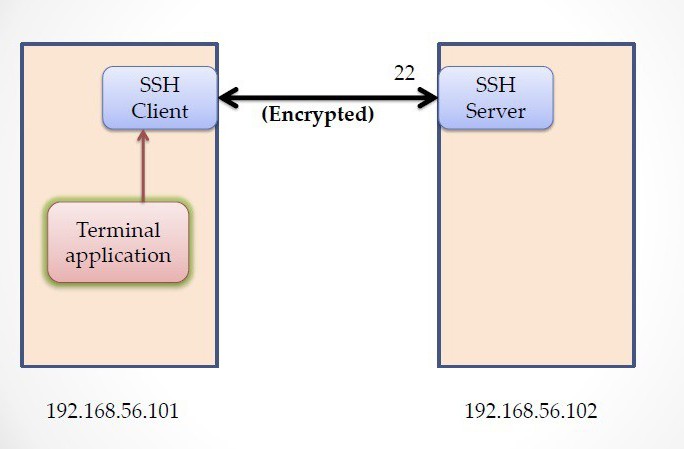
To reconfigure the router with the allocation for a specific program or process necessary conditions will have to perform port forwarding SSH. What is it? This is the purpose of a particular access for a specific program that uses an Internet connection, regardless of what setting the current communication Protocol (IPv4 or IPv6).
Technical feasibility
As is clear, the standard SSH port 22 is not always used. However, there is need to allocate some of the characteristics and parameters used during configuration.
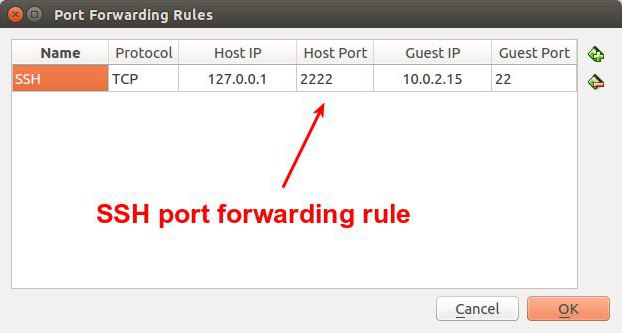
Why the confidentiality of the encrypted data transmission involves the use of the SSH Protocol in the form of exclusively external (guest) user port? Yes, because the applied tunneling allows the use of so-called remote shell (SSH), to access the terminal through remote login (slogin), and apply the procedure of the remote copy (scp).
In addition, the SSH port can be used in the case when the user needs to perform remote scripting, X Windows, which in the simplest case represents the transfer of information from one machine to another, as already mentioned, with forced data encryption. In such situations, the most necessary will be the use of algorithms based on AES. It is a symmetric encryption algorithm, which originally provided for in the technology SSH. And use it not only possible, but necessary.
History implementation
The technology appeared a long time ago. Let us leave aside the question of how to do port forwarding of SSH, and will focus on how it all works.
Usually all boils down to use proxy-based Socks, or you can use a tunneling VPN. If some kind of software application is able to work with VPN, it is better to prefer this option. The fact that almost all known programs that use the Internet traffic, a VPN can work, and setting up special routing is not working. It is, as in the case of proxy servers, allows you to leave an external address terminal, which at the moment is access to the network, unrecognized. That is, in the case of a proxy address is constantly changing, and the VPN remains the same with fixing a specific region different from that where there is a ban access.
The very same technology that opens the port SSH was developed in 1995 at the Technological University of Finland (SSH-1). In 1996, there was added improvement in the SSH-2 Protocol, which has received quite a large spread in the post-Soviet space, although this, as well as in some countries of Western Europe, it is sometimes necessary to obtain permission to usesuch a tunnel, and from government agencies.
The Main advantage of the open SSH-port, unlike telnet or rlogin, is the use of digital signatures RSA or DSA (using a pair in open and buried the key). In addition, in this situation, can use so-called session key based on Diffie-Hellman key exchange, which involves the use of symmetric encryption on the output, although it does not preclude the use of asymmetric encryption algorithms in data transmission and reception.
Servers and shell
In Windows or in Linux, the SSH port open is not so difficult. The only question is what kind of tools for this purpose will be used.
In this sense, you need to pay attention to the question of information transfer and authentication. First, the Protocol itself is sufficiently protected from the so-called sniffing, which is a very ordinary “wiretapping” traffic. SSH-1 was vulnerable to attacks. Interference in the data transfer process in the form of the scheme “middle man” had their results. Information can be easy to intercept and decipher quite elementary. But the second version (SSH-2) was immune from such kind of interference is called session hijacking, and thus is most prevalent.
Bans security
As for security for data sent and received, the organization connection, created with the use of such technologies, allows you to avoid the following problems:
- Identification key to the host at the stage of transmission, when using a “cast” fingerprint;
- Support for Windows and UNIX-like systems;
- Spoofing IP addresses and DNS (spoofing);
- Interception of passwords with physical access to the data transfer channel.
Actually, the whole organization of such a system built on the principle of "client-server”, that is, first and foremost the user's computer through a special program or add-in accesses the server, which produces the corresponding redirect.
Tunneling
Needless to say that the implementation of this kind in the system must be installed with a special driver.
Usually in the Windows system is embedded in a software shell Microsoft driver Teredo, which is a kind of virtual tool emulation of IPv6 networks with IPv4-only. Tunnel adapter default is in the active state. In case of occurrence of faults associated with it, you can just restart the system or execute the commands shutdown and restart the shell. To deactivate, use the following lines:
- Netsh;
- Interface teredo set state disabled;
- Interface isatap set state disabled.
After entering the command you should restart. To re-enable the adapter and verify its status is disabled prescribed permission enabled, and then, again, you must restart the entire system.
SSH server
Now look what port SSH is used as the core, starting from the scheme “client-server”. Usually the default 22 port, but as mentioned above, it can use 443. The only question is the preference of the server itself.
The Most common SSH servers are considered to be the following:
- For Windows: Tectia SSH Server, Cygwin with OpenSSH, MobaSSH, KpyM Telnet/SSH Server, WinSSHD, copssh, freeSSHd;
- FreeBSD: OpenSSH;
- Linux: SSH Tectia Server, ssh, openssh-server, lsh-server, dropbear.
All of the servers are free. However, you can find paid services which offer high level security, which is essential for the organization of network access and information protection at the enterprises. The cost of such services now is not discussed. But in General we can say that it is relatively inexpensive, even in comparison with the installation of specialized software or “iron” firewall.
SSH client
Change the SSH port can be based on client software and the appropriate settings when port forwarding on the router.
However, if you touch your client shells for different systems may include the following software products:
- Windows – SecureCRT, PuTTYKiTTY, Axessh, ShellGuard, SSHWindows, ZOC, XShell, ProSSHD, etc.;
- Mac OS X: iTerm2, vSSH, NiftyTelnet SSH;
- Linux and BSD: lsh-client, kdessh, openssh-client, Vinagre, putty.
Authentication based on public keys and changing the port
Now a few words about how the verification and configuration of your server. In the simplest case, it is necessary to use a configuration file (sshd_config). However, you can do without it, for example, in the case of using programs like PuTTY. To change the SSH port from the default value (22) to any other is completely elementary.
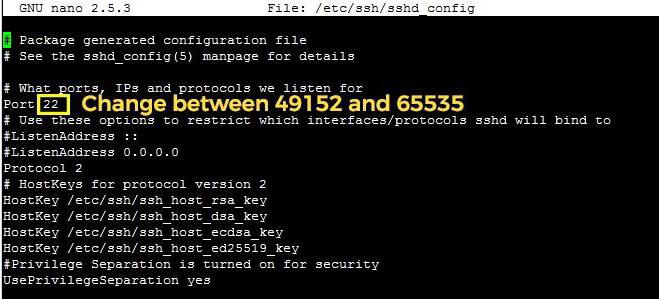
Most Importantly – to the room opened port does not exceed the value 65535 (ports just does not happen in nature). Moreover, you should pay attention to some open default ports that can be used by clients like MySQL databases or FTPD. If you specify SSH for its configuration, of course, those simply will not work.
It is Worth considering that the same Jabber client has to be run in the same environment using the SSH server on the virtual machine. And the localhost should be assigning the value 4430 (not 443 as noted above). This configuration can be used in the case where access to the main file jabber.example.com is blocked by a firewall.
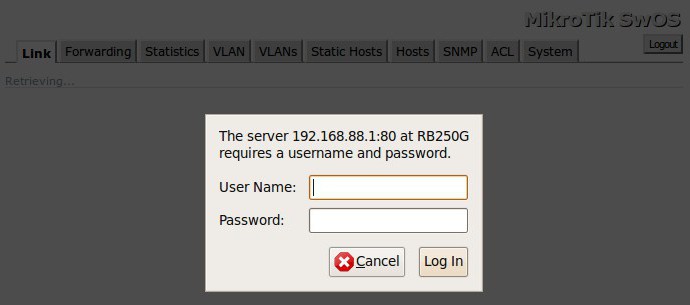
On the other hand, it is possible to throw ports on the router, using the configuration of its interface with the creation of exclusion rules. On most models the entrance through the input addresses beginning with 192.168 with the addition of 0.1 or 1.1, but on the routers, combining capabilities of ADSL modems like Mikrotik, destination address involves the use of 88.1.
This creates a new rule, then set the required parameters, for example, to install the external connection dst-nat and the ports are not manually prescribed in the General settings, and under preferences, action (Action). Nothing particularly difficult here. Main – to specify the necessary settings and set correct port. By default, you can use port 22, but if you use a custom client (some of the above for different systems), the value can be changed arbitrarily, but only so that this parameter does not exceed the declared value above which the port numbers are simply not available.
When configuring the connection should also pay attention to the parameters of the client software. It may well be that in its settings you need to specify a minimum key length (512), although the default usually set to 768. It is also desirable to set the timeout logon to 600 seconds and the remote access permission using root. After applying these settings, you need to give permission to use all rights authentication, except those that are based on the usage .rhost (but this is just system administrators).
In addition, if the user name registered in the system, does not coincide with the input at the moment, you will need to specify it explicitly, using the ssh user command the master can enter additional parameters (to those who understand what it is about).
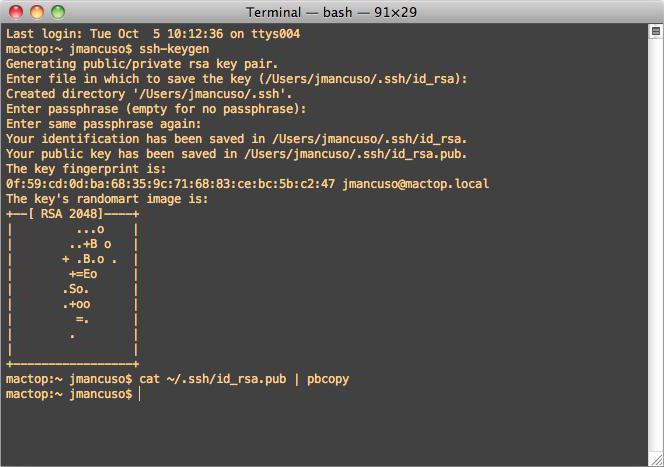
To convert the key and the encryption method can be used the command ~/.ssh/id_dsa (or rsa). To create a public key is the transformation with the help of strings ~/.ssh/identity.pub (but not necessarily). But, as practice shows, it is easiest to use commands like ssh-keygen. Here is the crux of the matter comes down only to add the key to available instruments of authorization (~/.ssh/authorized_keys).
But we had gone too far. If you go back to the question settings SSH port, as is clear, change the port of SSH is not so difficult. However, in some situations, that is, will have to sweat, as you will need to consider all values of the main parameters. Otherwise the question settings reduced either to the entrance in the server or the client software (if provided originally) or to use port forwarding on the router. But even in the case of changing the port 22, the default, to the same 443, it should be clearly understood that this scheme does not always work, but only in the case of installing the same add-in Jabber (other similar can use and their corresponding ports that are different from the standard). In addition, special attention should be given to setting parameters SSH client, which will directly interact with an SSH server, if it really is supposed to use the current connection.
Otherwise, if the port forwarding is not provided initially (although it is desirable to perform such actions), settings and options for access via SSH you can not change. There are special problems when creating a connection and its further use, in General, is not expected (unless, of course, is not to be used manual configuration server-based and client). The most common create exception rules on the router allows you to fix all problems or avoid them altogether.
Article in other languages:
AR: https://tostpost.com/ar/computers/7430-ssh.html
JA: https://tostpost.com/ja/computers/7430-ssh.html
PT: https://tostpost.com/pt/computadores/13272-como-configurar-e-usar-a-porta-ssh-passo-a-passo.html

Alin Trodden - author of the article, editor
"Hi, I'm Alin Trodden. I write texts, read books, and look for impressions. And I'm not bad at telling you about it. I am always happy to participate in interesting projects."
Related News
Evolve: a review and system requirements
While looking for interesting entertainment, which provides entertainment, is to choose a quality project. Multiplayer online gaming on all media many, because to choose one is extremely difficult. If you are a fan of robotics, di...
Add printer HP LaserJet P1102: connection, settings
this article details and step by step will show you how to install the printer HP LaserJet P1102. In addition to this will be given its real technical features and cost. All this will allow the potential buyer to choose, and new o...
the FTP Protocol is included in the Internet standards used for transferring large amounts of information. The first specification, which was the data transfer Protocol, appeared in 1971. Since that time FTP capabilities expanded ...
As in "cs: GO" to get medals of different quality
the Question of how "cs: GO" to the medal, interested in each member of the multimillion player community. These awards recognize the user as a true admirer and fan of the shooter. To them it is not so difficult, because you need ...
Error 924 in Play: how to fix?
Quite often, many users of Android-devices in which the service Play Market or Google Play is “stitched” in the system, faced with a situation where the service itself begins to fail and displays a message containing t...
How to disable parental control in Windows 7?
With the release of new operating systems – Windows 7 many young users have experienced an unexpected problem with the fact that now, using the admin account, you can limit many capabilities of the computer....


















Comments (0)
This article has no comment, be the first!