Now - 06:24:50
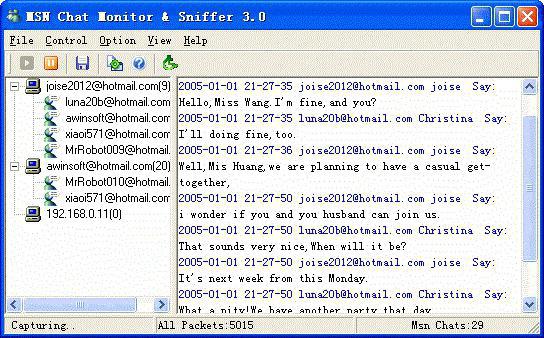
Network traffic analyser sniffer. What is a sniffer: description
Many users of computer networks, in General, unfamiliar to such a thing as a "sniffer". What is a sniffer, try and determine in simple language of an untrained user. But first, you still have to go into the predestination of the term.
Sniffer: what is sniffer from the point of view of the English language and computer technology?
In fact, to determine the essence of such software or software-hardware complex at all easy if you just translate the term.

This name comes from the English word sniff (sniff). Hence the value of the Russian term "sniffer". What is sniffer in our understanding? "Sniffer" that can monitor network traffic usage, and, basically, spy, which can interfere with local or Internet-centric networks, extracting the needed information based on access via the data transmission protocols TCP/IP.
Traffic Analyzer: how it works?
Say at once: sniffer, whether it is software or shareware-a software component able to analyze and intercept the traffic (transmitted and received data) exclusively through a network card (Ethernet). What happens?
Network interface is not always protected by the firewall (again – or “iron”), and therefore the interception of the transmitted or received data is only a trick.
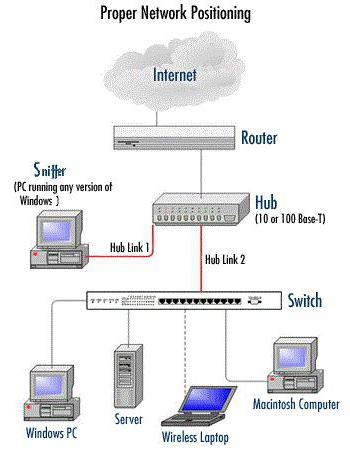
Inside the network the information is transmitted in segments. Within one segment assumes the distribution of data packets of all the devices connected to the network. Segmental information predrasuda on routers (routers), then at switches (switches) and hubs (hubs). Sending information is performed by partitioning the packets, so that the end user gets all the parts United together package from very different routes. Thus “listening” all potential routes from one subscriber to another, or the interaction of the Internet resource with the user can give not only access to unencrypted information, but also to some secret key, which can also be sent in this process of interaction. And then the network interface is completely unprotected, for the intervention of a third party.
Recommended
How to get out of "Skype" on the "Android" and not only
How to get out of "Skype" "Android"? This question bothers many users. The thing is that the messenger is not so difficult. But there are features that are only for mobile versions. To log out of Skype in this case more difficult than it seems. But i...
Kingo ROOT: how to use the program to gain administrative rights on Android
The Gadgets on the platform Android regained the lion's share of the market. Developers are continually perfecting the OS, trying to fit the needs of the users, but from year to year admit palpable mistake: forbid the owner to "stuffing" of his gadge...
How to get from Stormwind to Tanaris: practical tips
World of Warcraft is an iconic MMORPG, uniting millions of players around the world. There are many locations and puzzles, secret trails and larger, but rather dangerous paths. Sooner or later, every player chose the side of the Alliance, we have to ...
Well-intentioned and malicious purposes?
The Sniffers can be used for harm and for good. Not to mention the negative impact, it should be noted that such software and hardware systems are frequently used by system administrators who try to track the user activity not only online, but also their browsing behavior in terms of visited resources, activated the download on computers or sending them.
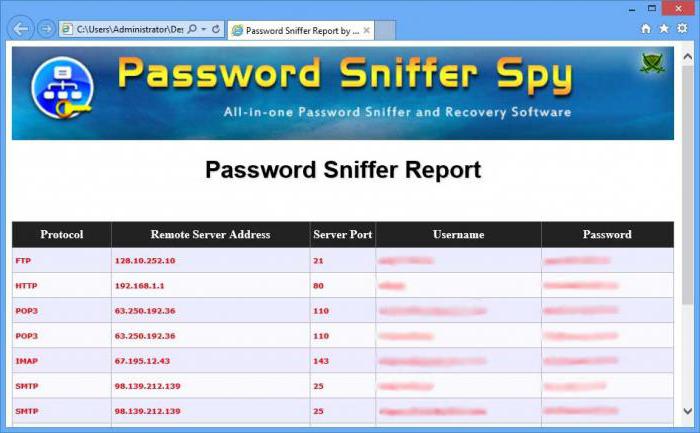
Methods for running the network analyzer is quite simple. Sniffer detects outgoing and incoming traffic of the machine. In this case we are not talking about internal or external IP. The most important criterion is the so-called MAC-address that is unique for any device connected to the global web. It is required to identify each machine on the network.
Types of sniffers
But the types can be divided into several osnovnih:
- Apparatue;
- Programmnye;
- Apparato-programmnye;
- Onlin-applet.
Behavioral determination of the presence of a sniffer on the network
To Detect the same WiFi sniffer can be on the network load. If you can see that the data transfer or the connection is not at a level declared by the provider (or allows a router), you should pay attention to it immediately.
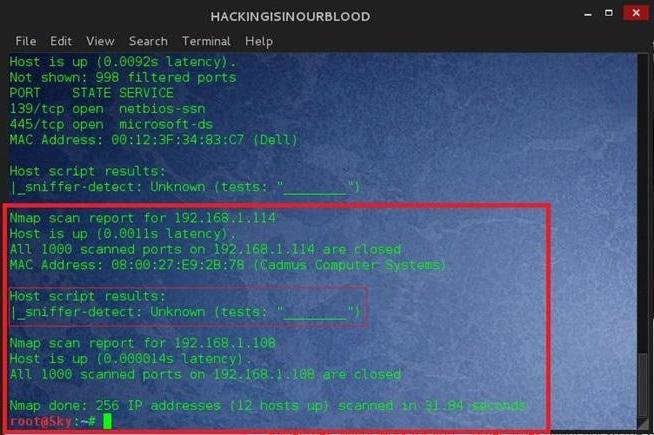
On the other hand, the provider can also run a sniffer to monitor the traffic without the user's knowledge. But, as a rule, the user did not even realize. But the organization that provides communication services and Internet connection, thus guarantee the user full security in terms of the interception of flooding, self-aligning customers ' heterogeneous peer to peer networks, Trojans, spyware, etc. But such funds are more programmatic and specific impact on the network or user terminals do not have.
Online resources
But particularly dangerous can be a traffic analyzer online type. The use of sniffers built a primitive system hacking. Technology in its simplest case is that initially, the attacker is logged on a specific resource, then loads the website picture. After confirmation of the download is given a link to the online sniffer, which is sent to a potential victim, for example, in the form of e-mail or SMS message with text like “You received a greeting from so-and-so. To open a picture (postcard), hit the link”.
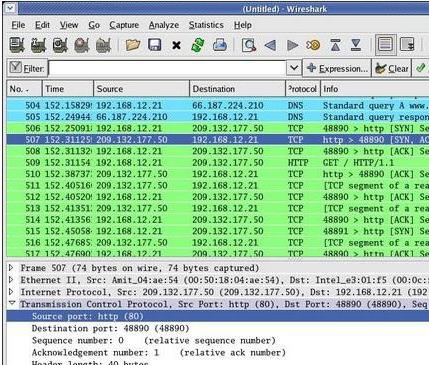
Naive users click on that hyperlink, the result of which is activated by the recognition and transfer of external IP address to the attacker. With the appropriate app it will be able not only to view any data stored on your computer, but also easily change the system setup from the outside, what a local userdon't even guess, taking such a change in the impact of the virus. But that's just the scanner when the test will be given zero threats.
How to protect against data interception?
Whether it's a Wi-Fi sniffer or any other analyzer system of protection against unauthorized scanning of the traffic is still there. One condition: they must be established only with the full confidence in “the wire”.
Such software is often called ‘antisniffer”. But if you think about it those same sniffers that analyze the traffic, but blocking other programs that attempt to gain unauthorized access.
Here is a legitimate question: is it worth it to install such software? Maybe its hacking by hackers inflict more damage, or it will block something that should work?
In the simplest case with Windows systems as protection is better to use the built-in firewall (firewall). Sometimes there may be conflicts with antivirus installed, but this often only applies to free packages. Professional purchased or activated monthly versions of these deficiencies deprived.
Instead of an epilogue
That's all for the concept of "sniffer". What is a sniffer, it seems that many have realized. Finally the question is different: how well such things would be to use the average user? And in fact, among young users is sometimes possible to notice a tendency to computer hooliganism. They think to hack a stranger “comp” is something like interesting competition or self-affirmation. Unfortunately, none of them thinks about the consequences, but to identify the attacker, using the same online sniffer, very simple by its external IP, for example, the website WhoIs. As a location, however, will indicate the location of the provider, however, country and city will be determined accurately. Well then it is small: either call the provider to block the terminal from which the unauthorized access or jurisdiction of the case. Draw your own conclusions.
When the installed program definition of dislocation of the terminal, which is trying to access, it is even easier. But the consequences could be disastrous, because not all users use the Xe anonymizers or virtual proxy servers and not even have a clue how to hide your IP on the Internet. And should learn…
Article in other languages:
HI: https://tostpost.com/hi/computers/4813-sniffer.html
JA: https://tostpost.com/ja/computers/4811-wikipedia-wikipedia.html
TR: https://tostpost.com/tr/bilgisayarlar/8563-a-analiz-r-trafik-sniffer-nedir-sniffer-a-klama.html

Alin Trodden - author of the article, editor
"Hi, I'm Alin Trodden. I write texts, read books, and look for impressions. And I'm not bad at telling you about it. I am always happy to participate in interesting projects."
Related News
Which hard drive best buy for computer, laptop, TV
As practice shows, no matter what initial volume had no drive, sooner or later, he will be missed. But when memory is short, comes to the decision to add or replace hard disk. In computer shops of these devices has enough. But whi...
The minimum and recommended L A Noire system requirements
L A Noire - a project from the company Rockstar in the genre of interactive detective and action from a third-person open world. The developers went for an experiment and stepped aside from the usual concept of GTA - explosions, c...
Creating a bootable USB drive using WinSetupFromUSB
Hello! Today we will consider the creation of a bootable USB drive. All the action will take place in the program WinSetupFromUSB. It is freely available, so you can download it absolutely free. In the archive with the progra...
How to make a booklet in Publisher? The creation and description
the publication of the booklet — is an effective way of presenting information about your product, company or services. To create a good program is Microsoft Publisher. To master it is not difficult. The remainder of this ar...
What is seeds, peers, the distribution of the torrent
this article will be considered “what are LEDs” and everything to do with the torrent. Because this service largely makes life easier for Internet users, enabling you to share a huge number of files. All presente...
Step by step instructions in the event of a message: "app launcher"an error has occurred
most operating systems, various gadgets, the most common was the platform “Android”. Along with a huge number of advantages that has this operating system, it has received a number of shortcomings. For example, in the ...

















Comments (0)
This article has no comment, be the first!