Now - 14:35:03
DDoS attack: how to do? Program for DDoS attacks
Probably, many users of computers and the Internet heard about the presence of DDoS attacks produced by hackers in relation to any of the sites or the servers of large companies. Let's see what is DDoS attack how to do it yourself and how to defend against such action.
What is DDoS attack?
For starters, perhaps it is necessary to understand what constitutes such misconduct. Say at once that in considering the topic, “DDoS attack: how to do it yourself” information is submitted solely for evaluation purposes and not for practical use. All actions of this kind a criminal offense.
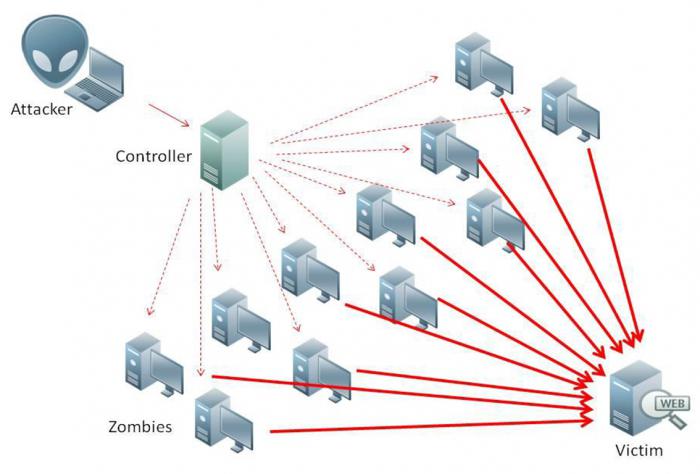
The attack Itself was, by and large, represents the sending of a large number of requests to the server or site that is in excess of the limit cases block the operation of the web resource or service provider in the form of a server outage protected firewalls or specialized equipment.
It is Clear that DDoS attack with their hands can not be created by one user with one computer terminal without special software. In the end, well he will not sit for days on end and constantly send requests to the attacked site. This will not work, because the protection from DDoS attacks provided by each provider, and one user is unable to provide this amount of queries to the server or website, which would in a short time has exceeded the limit of applications has triggered a variety of defense mechanisms. So to create your own attack will have to use something else. But more on that later.
Recommended
How to get out of "Skype" on the "Android" and not only
How to get out of "Skype" "Android"? This question bothers many users. The thing is that the messenger is not so difficult. But there are features that are only for mobile versions. To log out of Skype in this case more difficult than it seems. But i...
Kingo ROOT: how to use the program to gain administrative rights on Android
The Gadgets on the platform Android regained the lion's share of the market. Developers are continually perfecting the OS, trying to fit the needs of the users, but from year to year admit palpable mistake: forbid the owner to "stuffing" of his gadge...
How to get from Stormwind to Tanaris: practical tips
World of Warcraft is an iconic MMORPG, uniting millions of players around the world. There are many locations and puzzles, secret trails and larger, but rather dangerous paths. Sooner or later, every player chose the side of the Alliance, we have to ...
Why is there a threat?
If you understand what is DDoS attack how to make it and send you have exceeded the number of requests to the server, it is worth considering the mechanisms by which such actions are performed.
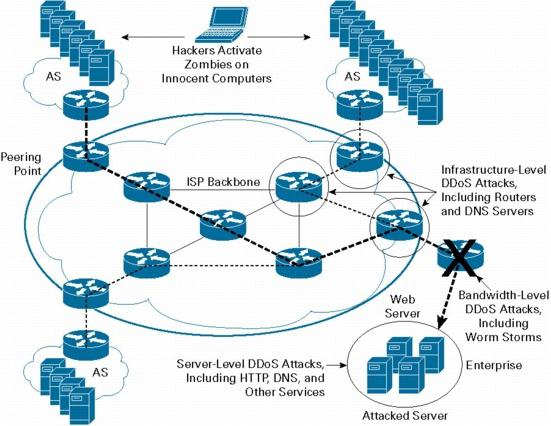
It can be unreliable and firewalls are not able to cope with a huge number of queries, gaps in the security system provider or in the "OSes" lack of system resources for processing the incoming requests further system hanging or emergency shutdown, etc.
At the beginning of the occurrence of such a phenomenon is basically a DDoS attack with their hands was carried out mainly by the programmers who created and tested the efficiency of the protection systems. Incidentally, at the time, from criminals who used as weapons components DoS and DDoS, suffered even such IT giants like Yahoo, Microsoft, eBay, CNN and many others. The key in those situations was an attempt to eliminate competitors in terms of restricting access to their Internet resources.
In General and modern electronic traders do the same. To do this just downloaded the program for DDoS attacks, well, then, as they say, a trick.
Types of DDoS attacks
Now a few words about the classification of these types of attacks. Basic to all is the removal of server or site failure. The first type include errors associated with sending incorrect instructions to the server to perform, resulting in a crash of his work. The second option – mass sending user data, leading to infinite (cyclic) test of increasing load on system resources.
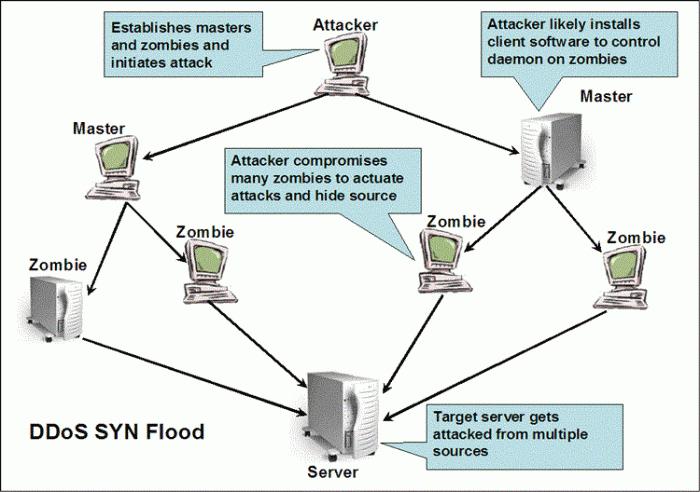
The Third type-flood. As a rule, this task beforehand malformed (meaningless) queries the server or network hardware to increase load. The fourth type-the so-called clogging of channels of communication about addresses. Can be used attack, leading to the fact that most computer system configuration is changed, leading to its complete failure. In General, the list can be long.
DDoS attack on the site
As a rule, this attack is associated with a specific hosting service and is aimed solely at single pre-defined web resource (in the example in the photo below labeled example.com).
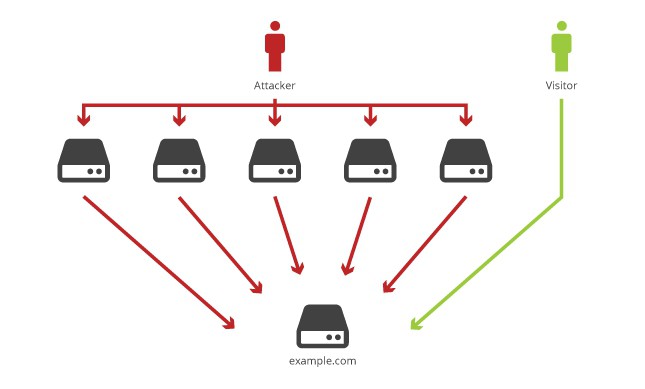
If there are too many requests to the site communication occurs because of the blocking connection, not the site itself, and the backend service provider, rather, not even the server itself or the system of protection and support. In other words, such attacks are directed to the owner of the hosting service received from the provider of the denial of service above a certain contractual limit traffic.
DDoS attack on the server
As for server attacks, they are not aimed at any particular hosting service, namely the service provider that provides it. And no matter what that may be affected site owners. The main victim is the provider.
Application for the organization of DDoS-attacks
Here we come to the understanding that such DDoS-attack. How to make it using specialized tools, we now face it. Just note that this type of application especially classified and are not. On the Internet they are available for free download. For example, the simple and well known program for DDoS attacks called LOIC freely posted on the world wide web for download. With its help, you can only attack sites and terminals with known URLS and IP addresses.
How to get an order in his IP address of the victim, for ethical reasons, we now will not be considered. Assume that the initial data we have.
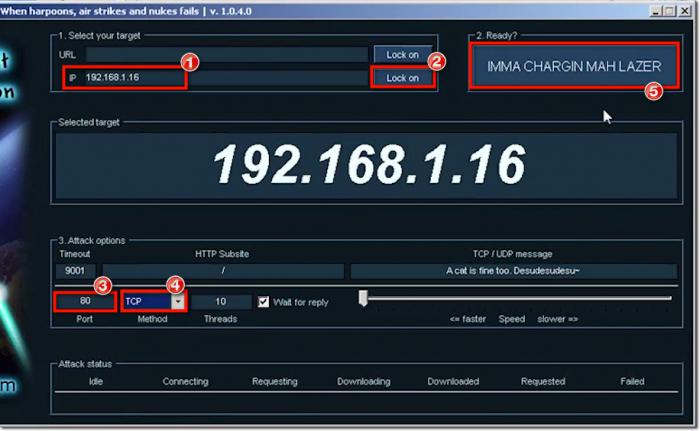
To run the application use executable file Loic.exe then in the top two rows on the left side to fit the original address, and then pressed two buttons called "Lock on” - a little to the right in front of each row. After that, the window will appear the address of our victim.
From the Bottom there are sliders to control the speed of sending requests to TCP/UDF, and HTTP. By default, the value put on “10”. Increase to the limit, and then push the big button "IMMA CHARGIN MAH LAZER” to begin the attack. To stop it is by pressing the same button.
Of Course, one such program, often called "laser cannon" to put some serious resource or provider will not work because protection from DDoS-attacks there are powerful enough. But if a group of persons to apply to a dozen or more guns at the same time, can be something to achieve.
Anti-DDoS
On the other hand, anyone who tries to attempt a DDoS attack, need to understand that “the” side is also not fools. They can easily calculate the address from which this attack is made, and it is fraught with sad consequences.

With regard to ordinary owners of hosting, it is usually provider immediately provides a package of services with appropriate protection. Means to prevent such actions can be very much. That is to say, redirect attack the attacker, the redistribution of requests across multiple servers, traffic filtering, redundancy protection systems to prevent false triggering, capacity resources, etc. By and large, a normal user is nothing to worry about.
Instead of an epilogue
It Seems, from this article it becomes clear that to do a DDoS attack yourself if you have a special and FOR some initial data were not working. Another thing is – whether to do it, and even inexperienced user who decided to play around just for sport? Everyone needs to understand that his actions in any case will cause retaliatory measures on the part of the attacked party, and, as a rule, not in favor of the user who started the attack. But, according to the Penal codes of most countries, for such actions can get, as they say, in places not so remote for a couple years. Who wants it?
Article in other languages:
AR: https://tostpost.com/ar/computers/5072-ddos.html
BE: https://tostpost.com/be/kamputary/9029-ddos-ataka-yak-zrab-c-pragrama-dlya-ddos-napada.html
HI: https://tostpost.com/hi/computers/5075-ddos-ddos.html
JA: https://tostpost.com/ja/computers/5072-ddos-ddos.html
PT: https://tostpost.com/pt/computadores/9028-ddos-ataque-como-fazer-programa-para-ataques-ddos.html
TR: https://tostpost.com/tr/bilgisayarlar/9037-ddos-sald-r-nas-l-program-ddos-sald-r-lar-i-in.html
UK: https://tostpost.com/uk/komp-yuteri/9033-ddos-ataka-yak-zrobiti-programa-dlya-ddos-atak.html

Alin Trodden - author of the article, editor
"Hi, I'm Alin Trodden. I write texts, read books, and look for impressions. And I'm not bad at telling you about it. I am always happy to participate in interesting projects."
Related News
How to update Warface: instructions for use
today the network has a huge number of different enterprise projects which are worth to pay attention to them. But not all of them can confidently stand in the market and to expand its audience of users. Although sometimes there a...
Base KV ТХ8: the arrangement of features
"Clash of thrones" is a strategy game. In it you will lead a clan that is at war with all other clans. Here mixed a variety of genres: role-playing, and tactics, and even tower defence. A feature of this project is the fact that y...
How to write to developers "Vkontakte" and to correctly apply
Social network called "Vkontakte" for a long time is popular. Constant updates, original design and many other factors made the social network one of the most popular products on the virtual market."Vkontakte": a bit about the nua...
How to put an accent in Word at the right letter?
oddly enough, not everyone knows how to put the accent in the Word. This is due to the extremely rare need for this feature among users. The Word contains, and many other diverse opportunities that most people don't even realize. ...
What is the reader, and what is it for
Many people are interested in the question: "What is reader and what functions it performs?" In short - is a device designed to read information from memory cards used in digital cameras, PDAs, mobile phones and other devices. Som...
How to split a hard disk into two partitions? Software for dividing hard drive
Every PC user faced with the need to partition the hard drive into two parts. Most often this procedure is required after the purchase of a computer or laptop (or hard drive). By default, the disk is only one partition. It will su...



















Comments (0)
This article has no comment, be the first!